Login Methods
After you have an account on Nightingale, log in to the system using an Secure Shell (SSH) client on your local desktop or laptop. Because of the added security for Nightingale, you will first log in to Nightingale’s secure node and then log in to a general access login node or, for groups that have them, a specialized interactive node.
Node Hostnames
Secure Node Hostname
ngale-bastion-1.ncsa.illinois.edu
General Access Login Nodes Hostnames
ng-login01.ngale.internal.ncsa.edu
ng-login02.ngale.internal.ncsa.edu
Specialized Interactive Node Hostname
NODENAME.ngale.internal.ncsa.edu
NODENAME will be something of the form ng-ai22, ng-gpu-h35, or ng-gpu-m37.
Note
Your PI can tell you if your allocation has a specialized interactive node and if so, its hostname.
All Nightingale users have access to the general access login nodes (ng-login01 and ng-login02). These nodes are a shared resource for all system users, limit your use of them to editing, compiling, and building your programs.
General Login Process
To log in to Nightingale, establish an SSH connection to the secure node and then establish an SSH connection to your login or interactive node. These are the steps:
sshto the secure nodengale-bastion-1.ncsa.illinois.edu. (Replace<your_username>with your NCSA identity username.)ssh <your_username>@ngale-bastion-1.ncsa.illinois.edu
Enter your NCSA (Kerberos) password. Note, the terminal will not show your password (or placeholder symbols such as asterisks [*]) as you type.
Enter
1to send a push to the Duo app on your phone.Approve the push request on your phone.
After you approve the push, you will be at a prompt on the
ngale-bastion-1node that will look similar to:[<your_username>@ngale-bastion-1 ~]$
sshto your login or interactive node using the appropriate hostname, following this syntax:ssh <your_username>@ng-<node_name>
For example, this is the command for a user with the username
hiropand the node nameCPU03:ssh hirop@ng-CPU03
Note
Connecting to Nightingale using the vscode program is not currently supported by the system.
Jump Host Login Method
You can combine the secure and login node ssh commands into one by specifying the secure node as a jump host. The jump host is used to connect to your destination node without needing to execute the ssh command twice.
ssh -J <your_username>@ngale-bastion-1.ncsa.illinois.edu <your_username>@ng-<login_node>
For example, user test1 can log in to the Nightingale login node astro07 with the following command:
ssh -J test1@ngale-bastion-1.ncsa.illinois.edu test1@ng-astro07
After you enter the ssh command:
Enter your NCSA (Kerberos) password, when prompted.
Approve the NCSA Duo push notification on your phone.
Again, enter your NCSA (Kerberos) password, when prompted.
Command-line SSH Clients
SSH is a client-server architecture that provides a secure channel over an unsecured network. An SSH client is a program for securely logging in to and executing commands on a remote machine. SSH encrypts the data sent over an open network, such as the internet, so that it can’t be read by others.
Several SSH clients are available for accessing Nightingale. The client you use will depend on your workstation’s operating system.
Microsoft Windows
You can use the built-in SSH Client in Windows (version 10 and later) or select from several freely available third-party SSH clients. Third-party clients typically provide a graphical user interface (GUI) rather than a command-line interface. PuTTY is a popular choice; MobaXterm is another one.
Mac OS X
Mac OS X comes with a built-in open-source version of SSH called OpenSSH; access it via the Terminal application. PuTTY is also available for Mac OS X.
Linux
Linux has SSH built into it, use the Linux terminal application to connect via SSH. PuTTY is also available for Linux.
X Window Servers
Originally developed for Unix, the X Window System allows a program on one computer to open windows on another computer’s screen (usually your desktop/laptop). The program that runs on the Nightingale is called the client. The program that runs on your desktop/laptop computer is called the server. X Window servers are available for Microsoft Windows, Mac, and Unix/Linux.
One-Time Setup
Before logging in to Nightingale, complete these one-time steps to set up the connection.
XQuartz allows you to use an application from Nightingale and have its windows on your own computer.
Open the Terminal application on your Mac.
Enter the following command into the terminal:
cd ~/.ssh
Enter the following command into the terminal:
nano config
This will bring you into an editor program that looks like this:
UW PICO 5.09 File: config ^G Get Help ^O WriteOut ^R Read File ^Y Prev Pg ^K Cut Text ^C Cur Pos ^X Exit ^J Justify ^W Where is ^V Next Pg ^U UnCut Text ^T To Spell
This editor allows you to edit a configuration file that sets up connections to the outside world, so you don’t have to type as much all the time.
Copy and paste the following configuration file code block into your terminal. Before you run it, you will modify the code in the next steps.
Host ngb1 HostName ngale-bastion-1.ncsa.illinois.edu ControlMaster auto ControlPath /tmp/ssh_mux_%h_%p_%r ControlPersist 5h User YOUR_USERNAME Host ng-login01 HostName ng-login01.ngale.internal.ncsa.edu ProxyJump ngb1 User YOUR_USERNAME
Use the arrow keys to position your cursor and make the following modifications:
Replace
YOUR_USERNAMEwith your NCSA identity username.If you have an interactive node assigned to you, you can add second copy of the last stanza of the configuration file; in that stanza, replace
ng-login01with the name of your interactive node.
For example, a user with username
hiropand the assigned interactive nodeng-gpu-x07would have the following configuration file:Host ngb1 HostName ngale-bastion-1.ncsa.illinois.edu ControlMaster auto ControlPath /tmp/ssh_mux_%h_%p_%r ControlPersist 5h User hirop Host ng-login01 HostName ng-login01.ngale.internal.ncsa.edu ProxyJump ngb1 User hirop Host ng-gpu-x07 HostName ng-gpu-x07.ngale.internal.ncsa.edu ProxyJump ngb1 User hirop
After you finish modifying the file, press Control+O to write the file.
Press return (or Enter) to confirm the file name.
Press Control+X to exit the editor and you are back at the prompt.
MobaXterm enables an SSH connection and provides other useful utilities, such as file transfer and editing.
Download and install MobaXterm.
You can install either the Portable or Installer edition of MobaXterm. You will need to have admin privileges on your machine to install the Installer edition. The Portable edition does not require admin privileges, to use it extract the downloaded zip file and click mobaxterm.exe.
Launch the MobaXterm application and click Session in the upper left to start an SSH session.
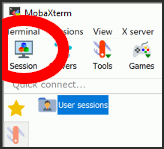
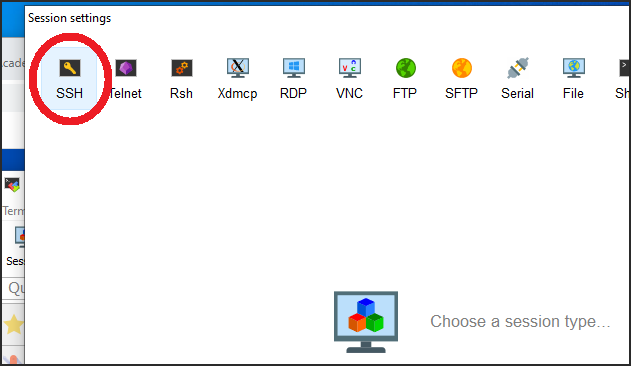
Select SSH from the session types and click OK.
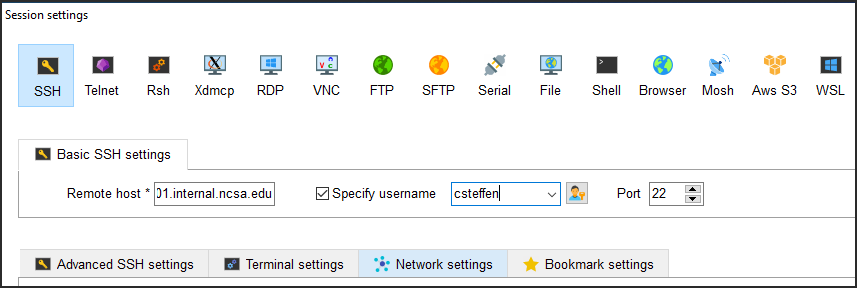
In the Basic SSH Settings tab:
In the Remote host box, enter the name of the login node you want to access (either a general access or interactive node).
Select the Specify username checkbox and enter your NCSA Identity username.
In the Network settings tab, click SSH gateway (jump host).
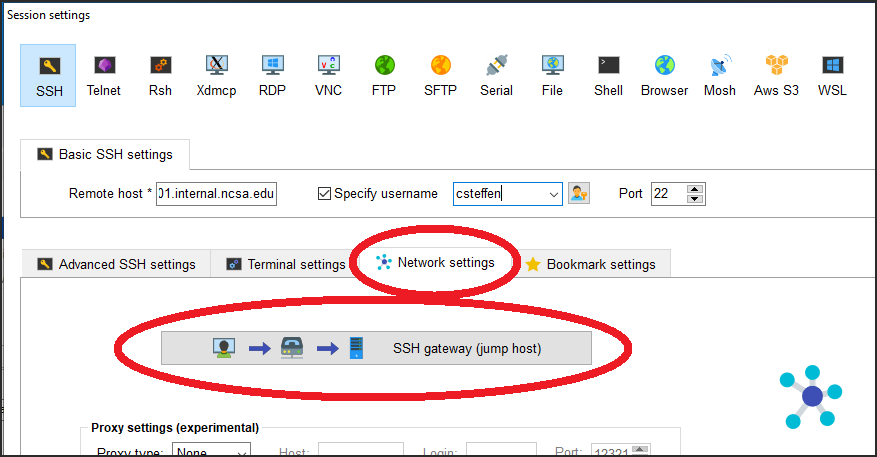
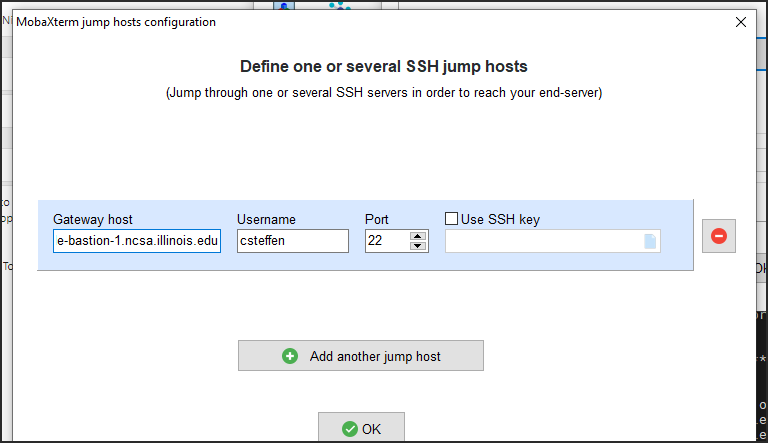
In the jump hosts configuration window:
In the Gateway host box, enter
ngale-bastion-1.ncsa.illinois.edu.In the Username box, enter your NCSA identity username.
Click OK.
You may see a warning message saying that your remote host identification has changed; click Yes to continue.
You should now be back in the Session settings window. Click OK to initiate your SSH connection.
A terminal window will be displayed asking for your password; enter your NCSA (Kerberos) password and press Enter.
Log in to Nightingale
After the preceding one-time setup is complete, follow these steps each time you want to log in to Nightingale.
Enter the following into the terminal (if you are logging in to an interactive node, replace
ng-login01with the name of that interactive node):ssh -X ng-login01
If you see a message that begins “The authenticity of host….” and ends with “Are you sure you want to continue connecting (yes/no/[fingerprint])?”, enter
yes.Enter your NCSA (Kerberos) password at the prompt. Note, the terminal will not show your password (or placeholder symbols such as asterisks [*]) as you type.
There will be a Duo prompt asking for a passcode or for “option 1”. You may either:
Enter
1and approve the Duo push notification on your phone.
Or
Enter a 6-digit passcode from the NCSA entry of your Duo app.
Again, enter your NCSA (Kerberos) password at the prompt. Note, the terminal will not show your password (or placeholder symbols such as asterisks [*]) as you type.
You should have a prompt that reflects that you are on a Nightingale node. It will include
@ng-and look similar to this example for userhiropon nodeng-gpu-m01:[hirop@ng-gpu-m01 ~] $
You can load modules, run software, and access your files from here.
Open MobaXterm.
In the left bar, there is a list of User sessions, each one is a node that you have configured for logging in.
Right-click on the Nightingale node you want to log in to and select execute.
A window will pop up asking for your password. Enter your NCSA (Kerberos) password and press Enter or click OK.
A second window will pop up asking for your 2FA code.
On your phone, open the Duo app.
Select the NCSA entry (not the University of Illinois entry).
Enter the 6-digit passcode displayed in the Duo app into the pop-up window.
A black window without a prompt will appear. You may need to wait 30 seconds or a minute here.
When it asks for your password, enter your NCSA (Kerberos) password. Note, the window will not show your password (or placeholder symbols such as asterisks [*]) as you type.
You are now ready to work. You should have a prompt at the bottom and a file window on the left showing your directories on Nightingale.